Perception of Women In Security
For many years, service in the military or law enforcement h......

Usefulness of CCTV Footage
CCTV cameras are gaining popularity in the country. Once dep......

Intelligent CCTV: How Deep Learning Algorithms are Influencing The Next Generation of CCTV For Better
Artificial intelligence uses deep learning algorithms to ana......

REAL ESTATE By Blessmarked
Real estate refers to property in the form of land, building......
Latest News
Strengthening Data Protection for Kenyan Security Firm
We live in a rapidly growing digital space and data protection is an important aspect of cyber security. The Kenya Data Protection Act, 2019, requires Data Controllers and Processors to process......
Read MoreCCTV Surveillance in Schools: A Necessary Measure or an Invasion of Privacy?
As concerns over safety and security continue to rise, many educational institutions have turned to Closed-Circuit Television (CCTV) surveillance systems as a means of enhancing student and staf......
Read MoreClimate Change and Food Banks
Food banks are philanthropic non-profit establishments that serve as locations where individuals in need can get food and amenities. Communities frequently have food banks set up so that donated......
Read MoreSafety and Security, Definitions and Process
What is the difference between the term’s safety and security? Safety is used to refer to a condition where someone is protected from factors that are likely to cause harm to them in road accide......
Read MoreHuman Capital: The Key to Unlocking Security Technology’s Full Potential
In today’s rapidly evolving digital landscape, the importance of robust security technology cannot be overstated. However, the success of these technologies is not solely dependent on their tech......
Read MoreHow Artificial Intelligence (AI) Is Revolutionizing Security Scanners and Detectors
Security scanners are devices or systems designed to detect potential threats or prohibited items in various environments, such as airports, public venues, and high security facilities. They emp......
Read MoreSupply Chain Attacks and Critical Infrastructure: How CISA Helps Secure a Nation's Crown Jewels
What is Critical Infrastructure and Why is It Attacked?Critical infrastructure is the physical and digital assets, systems and networks that are vital to national security, the economy, public health,......
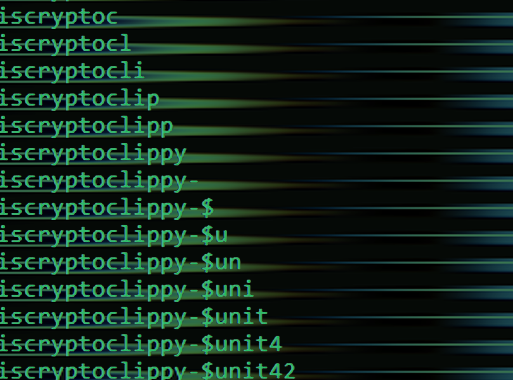
Read MoreCryptoClippy: New Clipper Malware Targeting Portuguese Cryptocurrency Users
Portuguese users are being targeted by a new malware codenamed CryptoClippy that's capable of stealing cryptocurrency as part of a malvertising campaign.The activity leverages SEO poisoning techniques......
Read MoreIsraeli cyber security website briefly taken down in cyberattack
One of Israel's largest cyber-security companies, Check Point, was taken down by a group of hackers calling themselves "Anonymous Sudan" on Tuesday afternoon.However, after a short while, the website......
Read MoreNorth Korean APT43 Group Uses Cybercrime to Fund Espionage Operations
A new North Korean nation-state cyber operator has been attributed to a series of campaigns orchestrated to gather strategic intelligence that aligns with Pyongyang's geopolitical interests since 2018......
Read More